What is a Man-in-the-Middle Attack?
A Man-in-the-Middle attack, often abbreviated as MitM, is a type of cyberattack where the attacker secretly intercepts and potentially alters the communications between two parties who believe they are directly communicating with each other. In essence, the attacker positions themselves “in the middle” of this exchange, hence the name.
This form of attack is particularly dangerous because it allows the attacker to eavesdrop on the communication, gather sensitive information and even manipulate the conversation by injecting new messages or altering existing ones. The victims, unaware of the attacker’s presence, continue to communicate believing they are interacting directly with each other.
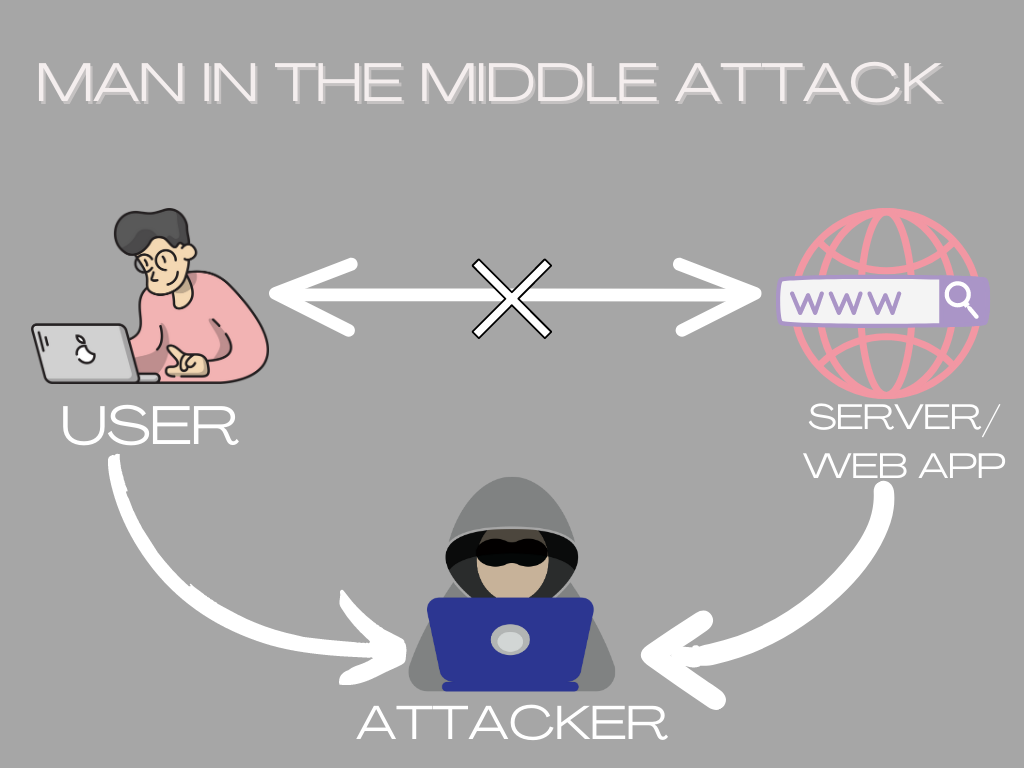
How Does a Man-in-the-Middle Attack Work?
The process of a MitM attack can be broken down into three main steps:
Interception
This is the initial and crucial step in a MitM attack where the attacker manages to insert themselves into the communication channel between two parties. There are several ways an attacker can achieve this:
- Packet Sniffing: This involves the use of software tools to capture data packets as they travel across a network. These tools can be used on unsecured networks or on secured networks where the attacker has managed to bypass security measures.
- IP Spoofing: The attacker can forge the IP packets to make them appear as if they are coming from a trusted source. This can trick the receiver into thinking they are communicating with a legitimate party, allowing the attacker to intercept the data.
- ARP Spoofing: In this method, the attacker sends fake ARP (Address Resolution Protocol) messages to a local area network. This can allow the attacker to link their MAC address with the IP address of a legitimate user on the network. As a result, data that is intended for the legitimate user is sent to the attacker instead.
- Wi-Fi Eavesdropping: If a user connects to an unsecured Wi-Fi network, or a network that the attacker has managed to compromise, the attacker can easily monitor the user’s online activity and intercept their data.
- Phishing: This involves tricking a user into voluntarily giving up their information. For example, the attacker might send an email that appears to be from a trusted source, asking the user to log in to a fake website where their username and password can be captured.
- DNS Poisoning: This is a type of MitM attack where the attacker manipulates the Domain Name System (DNS), which translates website names into IP addresses. The attacker replaces a legitimate IP address with a fake one on the DNS server. As a result, users trying to visit a specific website are redirected to a malicious one controlled by the attacker, where they can be tricked into providing sensitive information. This type of attack can affect many users if a widely-used DNS server is poisoned.
Decryption and eavesdropping
Once the attacker has successfully intercepted the communication, they can begin to monitor and capture the data being transmitted. This process involves two key steps:
Eavesdropping: This is the act of secretly listening to the private communication between the two parties. The attacker can use various tools to capture the data packets being transmitted and then analyze them to extract useful information. This could include personal details, login credentials, financial information and more.
Decryption: If the data being transmitted is encrypted, the attacker will need to decrypt it to access the sensitive information it contains. This can be a complex process and often requires significant computational resources. The attacker might use various techniques to achieve this, such as:
- Key Cracking: If the encryption used involves a key, the attacker might attempt to crack it using brute force or more sophisticated methods.
- Exploiting Weak Encryption: If weak encryption algorithms are used, the attacker might be able to exploit known vulnerabilities to decrypt the data.
- SSL Stripping: This involves downgrading a secure HTTPS connection to an insecure HTTP connection, allowing the attacker to view the data in plain text.
Injection and Alteration
This is the phase where the attacker, having successfully intercepted and decrypted the communication, can now manipulate the data being transmitted. This manipulation can take several forms:
- Message Injection: The attacker can create new messages and send them to one or both parties. For instance, they could send a message to a user pretending to be their bank asking for sensitive information.
- Message Alteration: The attacker can change the content of the messages being exchanged between the two parties. For example, they could alter the details of a financial transaction, redirecting the funds to their own account.
- Session Hijacking: The attacker can take over a session between a user and a service. For instance, if a user is logged into their online banking, the attacker could hijack this session and carry out transactions on behalf of the user.
- Malicious Redirection: The attacker can redirect the users to malicious websites. For example, they could alter a URL in a message leading the user to a phishing site designed to capture their login credentials.
Impact of Man-in-the-Middle Attacks
The impact of a successful MitM attack can be devastating. For individuals, this could mean the loss of sensitive information such as credit card details, social security numbers or login credentials. For businesses, a MitM attack could lead to significant financial loss, damage to reputation and loss of customer trust. In some cases, the data intercepted during a MitM attack could be used for further attacks, leading to even greater damage.
How to Prevent Man-in-the-Middle Attacks
Preventing MitM attacks involves a combination of good security practices and the use of advanced security technologies. Some effective strategies include:
- Use of Secure Networks: Public Wi-Fi networks are often unsecured, making them prime targets for attackers. Avoid conducting sensitive transactions such as online banking or accessing confidential work documents on public Wi-Fi. If you must use a public network use a Virtual Private Network (VPN) to encrypt your data and make it harder for an attacker to intercept.
- Regular Software Updates: Keeping your software up-to-date is crucial. Software developers regularly release updates that fix known security vulnerabilities that could be exploited by attackers. This includes your operating system, web browsers, antivirus software, and any apps or software you regularly use.
- HTTPS: Always check that the websites you visit use HTTPS (the lock icon in the address bar) which encrypts the data between your browser and the website. This can prevent an attacker from being able to read or modify any data you send or receive.
- Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring a second form of authentication in addition to your password. This could be a text message or email with a unique code, a fingerprint scan or a prompt from a trusted device. Even if an attacker manages to steal your password, they would still need the second factor to access your account.
- Security Awareness: Be aware of the common signs of a MitM attack, such as unexpected login prompts, sudden changes in the appearance of websites or unexplained account activity. Regularly check your account statements and online accounts for any unusual activity.
- Secure Configurations: Ensure that all devices including routers and other network equipment are securely configured. Default settings often prioritize convenience over security and may leave your device vulnerable to attacks. Change default passwords, disable remote management and enable automatic updates if available.
- Encryption: Use strong encryption for your data both at rest and in transit. This can prevent an attacker from being able to read your data even if they manage to intercept it.
- Firewalls and Intrusion Detection Systems (IDS): Use firewalls to block unauthorized access to your network and IDS to monitor your network for any suspicious activity.
Conclusion
Man-in-the-Middle attacks pose a significant threat in today’s digital world. However, by understanding what they are, how they work and how to prevent them, individuals and organizations can significantly reduce their risk. Remember, the key to effective cybersecurity is not only the use of advanced technologies but also continuous education and vigilance.
For more articles click HERE



